PAGE CONTENT:
In an age where digital threats are becoming increasingly sophisticated, system-level protection has become more critical than ever. One of the core components of Microsoft's security architecture is Secure Boot — a feature designed to ensure that your PC boots using only software that is trusted by the Original Equipment Manufacturer (OEM). Introduced with Windows 8 and enhanced in later versions like Windows 10 and 11, Secure Boot has become essential in both consumer and enterprise environments. This article explores Secure Boot in depth: what it is, how it works, its benefits, and how to manage it.

What is Secure Boot?
Secure Boot is a security standard developed by members of the Unified Extensible Firmware Interface (UEFI) Forum. It is designed to prevent unauthorized or malicious code from loading during the system start-up process. When enabled, Secure Boot uses cryptographic signatures to validate boot software, including the operating system loader, drivers, and UEFI applications.
Unlike the older BIOS system, which does not verify the integrity of boot components, Secure Boot ensures that every component in the boot chain is digitally signed by a trusted authority. This adds a critical layer of defense against threats like rootkits, which can load before the operating system and remain hidden from traditional antivirus software.
Benefits of Secure Boot
Secure Boot offers numerous benefits, particularly in protecting against low-level attacks that could compromise the system before the OS even starts:
1. Protection Against Rootkits and Bootkits
These types of malware embed themselves in the boot process. Secure Boot blocks them by validating the digital signatures of all boot components, preventing the execution of unsigned or tampered code.
2. Verified Boot Integrity
Only signed operating system loaders and drivers are allowed to execute, ensuring that no unauthorized code can hijack the system during boot-up.
3. Enhanced Security for Enterprises
For corporate networks, Secure Boot helps enforce compliance and ensures that endpoints are running approved software, forming a foundational component of Zero Trust security models.
4. Seamless Integration with Other Security Features
Secure Boot complements features like BitLocker Drive Encryption, Windows Defender Credential Guard, and Trusted Platform Module (TPM) to provide a comprehensive security posture.
Secure Boot Requirements
To use Secure Boot, both hardware and software requirements must be met:
1. Hardware Requirements
- UEFI Firmware: Secure Boot requires UEFI (not Legacy BIOS).
- Secure Boot Compatible Motherboard: Most modern motherboards support this feature.
- Trusted Platform Module (TPM): While not mandatory, TPM enhances system security when used alongside Secure Boot.
2. Operating System Requirements
- Windows 8 and Newer: Secure Boot is supported on Windows 8, 8.1, 10, and 11.
- Windows 11 Mandatory Requirement: Secure Boot must be enabled for Windows 11 installation on new hardware.
3. Boot Mode
Secure Boot requires the system to be booted in UEFI mode, not Legacy BIOS mode. This setting can be adjusted in the firmware setup.
How Secure Boot Works?
The Secure Boot process relies on a digital certificate chain to verify each boot component. Here's a breakdown of how it functions:
1. UEFI Firmware
When the PC is powered on, the UEFI firmware initiates the Secure Boot process. The firmware checks the bootloader's signature against a database of trusted certificates (usually including Microsoft's key by default).
2. Signature Verification
If the bootloader is signed by a trusted certificate, the system allows it to execute. Otherwise, the boot process halts, and an error message such as "Secure Boot Violation" is displayed.
3. Windows Boot Manager
Once verified, the bootloader hands control over to the Windows Boot Manager, which continues the boot process by loading the Windows kernel and essential drivers.
4. Trusted Certificate Store
Secure Boot uses four databases stored in firmware:
- Allowed Signature Database (db)
- Forbidden Signature Database (dbx)
- Key Enrollment Key (KEK)
- Platform Key (PK)
These databases are used to manage which software is allowed or blocked during the boot process.
How to Enable or Disable Secure Boot?
Managing Secure Boot can be necessary for tasks like installing Linux, running older operating systems, or testing unsigned drivers. Here's a guide to enable or disable it:
Step 1: Access UEFI Firmware Settings
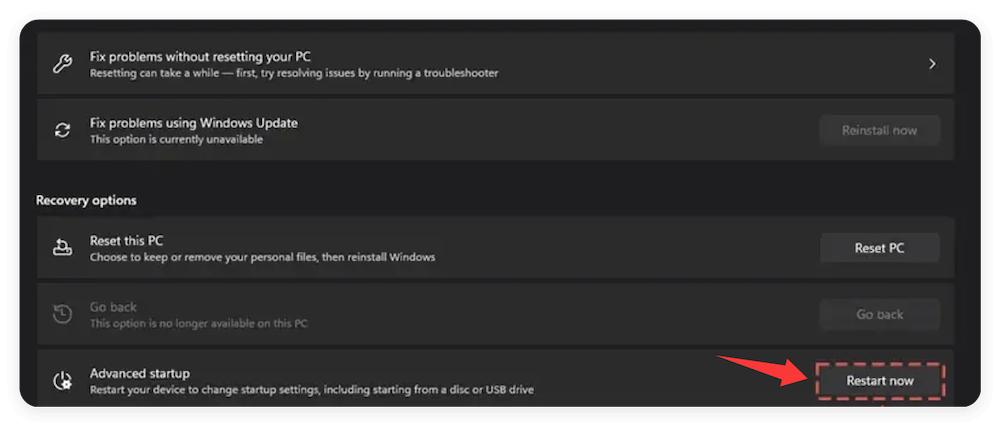
- Go to Recovery from Update & Security via Settings.
- Under Advanced startup, click Restart now.
![Windows Secure Boot]()
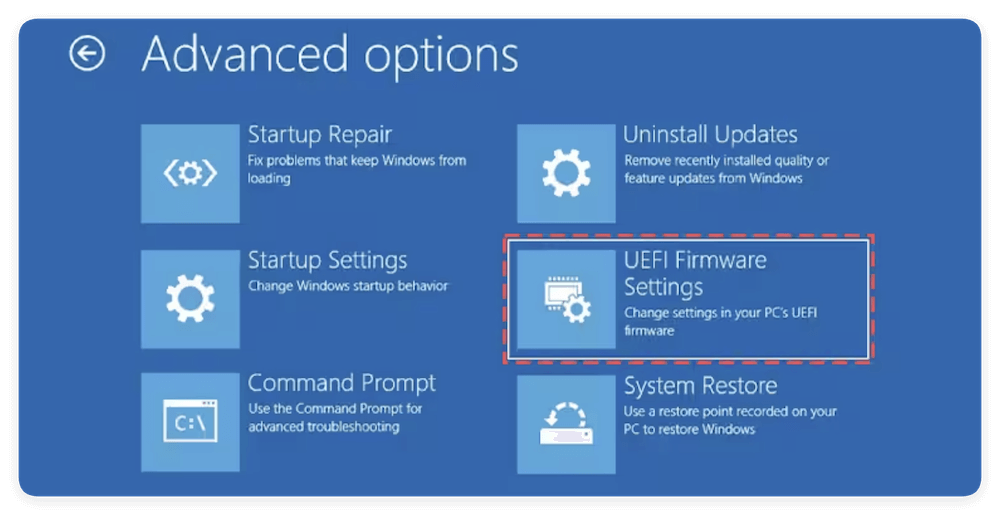
- Select UEFI Firmware Settings from Advanced options via Troubleshoot.
- Click Restart.
![Windows Secure Boot]()
Step 2: Enable/Disable Secure Boot
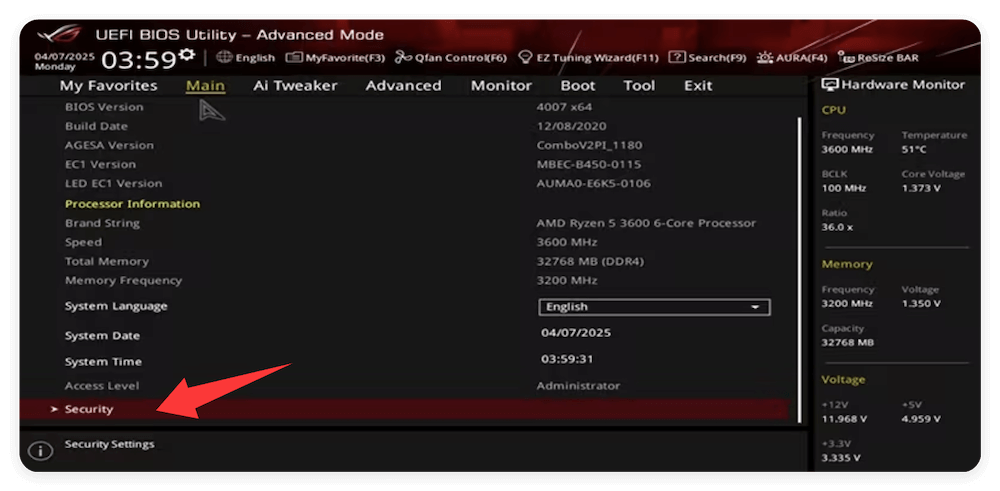
- Once in UEFI setup, move to the Boot or Security tab.
![Windows Secure Boot]()
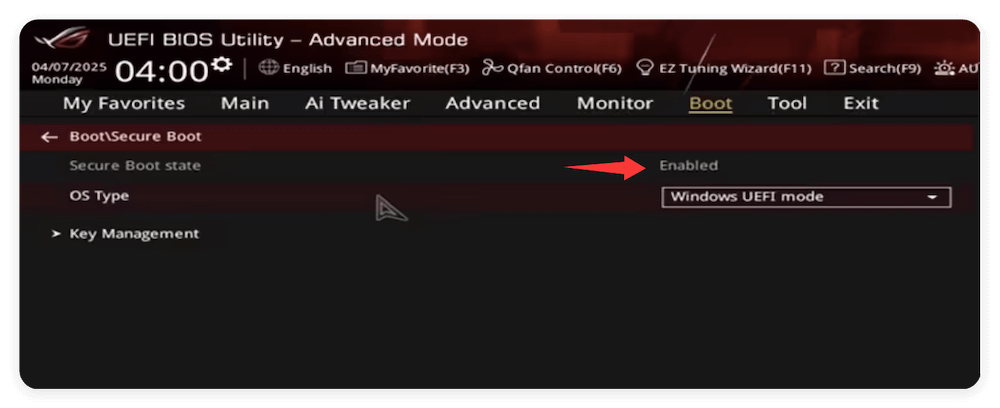
- Look for the Secure Boot setting. Toggle it to Enabled or Disabled.
![Windows Secure Boot]()
- Save and exit the firmware setup (usually by pressing F10).
💡 Note: Disabling Secure Boot may prompt the system to convert to Legacy Boot mode or display a warning.
Common Issues and Troubleshooting
While Secure Boot significantly enhances system protection, it can sometimes introduce compatibility problems.
1. Secure Boot Violation
This occurs when the system tries to boot an unsigned or untrusted bootloader. To fix:
- Re-enable Secure Boot and ensure OS is signed.
- Clear the dbx if it mistakenly contains revoked certificates.
- Reinstall the operating system in UEFI mode.
2. Dual-Booting Linux
Many Linux distributions are not signed by Microsoft's key and may not boot under Secure Boot. Solutions include:
- Using signed bootloaders (like Ubuntu's GRUB with Shim).
- Disabling Secure Boot temporarily.
- Enrolling custom keys via UEFI (advanced users).
3. Driver or Hardware Incompatibility
Older drivers or expansion cards might be unsigned. Ensure your hardware supports Secure Boot, or obtain updated drivers from manufacturers.
Secure Boot and Windows Security Features
Secure Boot works in tandem with several other Windows security mechanisms to create a robust defense system.
1. BitLocker
Secure Boot helps verify that the OS has not been tampered with before BitLocker decrypts the disk, ensuring boot-time integrity.
2. Windows Defender Credential Guard
This feature isolates secrets like login credentials using virtualization-based security (VBS). Secure Boot ensures this environment is protected from rootkits and bootkits.
3. Windows Hello and TPM
Secure Boot complements these technologies by safeguarding the trusted computing base. Together, they ensure biometric authentication operates in a secure environment.
4. Device Health Attestation
Organizations can use Device Health Attestation to verify that Secure Boot is enabled before allowing access to sensitive resources.
Secure Boot in Enterprise and IT Environments
Secure Boot is particularly valuable for enterprise IT and managed service providers (MSPs) looking to maintain system compliance and reduce risk.
1. Enforcement through Group Policy
Administrators can configure Windows Defender policies to enforce Secure Boot as a requirement for device compliance in Microsoft Endpoint Manager or Microsoft Intune.
2. Protecting Endpoint Devices
In enterprise environments, Secure Boot is used to ensure that laptops, desktops, and servers boot only into known, secure software environments—critical for Zero Trust security models.
3. Secure Boot Keys and Management
IT departments can customize Secure Boot keys to only trust in-house software or restrict devices from booting unauthorized operating systems.
4. Remote Attestation and Compliance
Secure Boot can be used alongside Windows Autopilot and MDM solutions to confirm system health and policy compliance remotely before granting network access.
Future of Secure Boot and Firmware Security
As threats evolve, so does the Secure Boot framework. Newer developments include:
1. Measured Boot
In addition to verifying components, Measured Boot logs each step of the boot process to the TPM. This allows remote systems to verify a machine's integrity using cryptographic hashes.
2. Secure Core PCs
Microsoft introduced Secured-core PCs, which combine Secure Boot, TPM 2.0, VBS, and hypervisor protections to provide deeper hardware-rooted security, ideal for industries like healthcare, finance, and government.
3. Enhanced Firmware Protections
Chipmakers and OEMs are implementing tighter controls around firmware updates, signed firmware images, and boot-level protection, making Secure Boot even more resilient.
Conclusion
Secure Boot is a cornerstone of modern Windows security. By verifying each component of the boot process, it ensures that your system starts in a known good state and is protected against stealthy, boot-level malware. Whether you're a home user looking for peace of mind or an IT administrator responsible for hundreds of endpoints, Secure Boot provides essential protection that should not be overlooked.
With growing support for Secure Boot across platforms and its integration into Windows 11's system requirements, understanding how it works—and how to manage it—is more important than ever. By enabling Secure Boot and combining it with other security features like BitLocker, TPM, and Windows Defender, you create a secure foundation that strengthens your system against both present and future threats.
Related Articles
- Oct 11, 2024What Is Time Machine?
- May 28, 2025About USB Ports: Everything You Need to Know
- Mar 19, 2025What is U Disk? A Comprehensive Guide
- Apr 29, 2025What is SSD TRIM, How to Enable or Disable TRIM on SSD on Windows?
- Jul 12, 2023What Is NVMe SSD? What Are the Advantages of NVMe SSD?
- May 26, 2025What's EFI Partition? Is It Safe to Delete the EFI Partition on Windows?

Coco Lin
Coco has been a writer and a chief programmer at Donemax software since 2018. Over 10 years of experience of writing troubleshooting articles in the software industry, she is passionate about programming and loves to providing solutions to Windows and Mac users. Also she enjoys music and palying tennis in her free time.

Gerhard Chou
In order to effectively solve the problems for our customers, every article and troubleshooting solution published on our website has been strictly tested and practiced. Our editors love researching and using computers and testing software, and are willing to help computer users with their problems
Hot Donemax Products

Clone hard drive with advanced clone technology or create bootable clone for Windows/Mac OS.

Completely and easily recover deleted, formatted, hidden or lost files from hard drive and external storage device.

Certified data erasure software - permanently erase data before selling or donating your disk or any digital device.